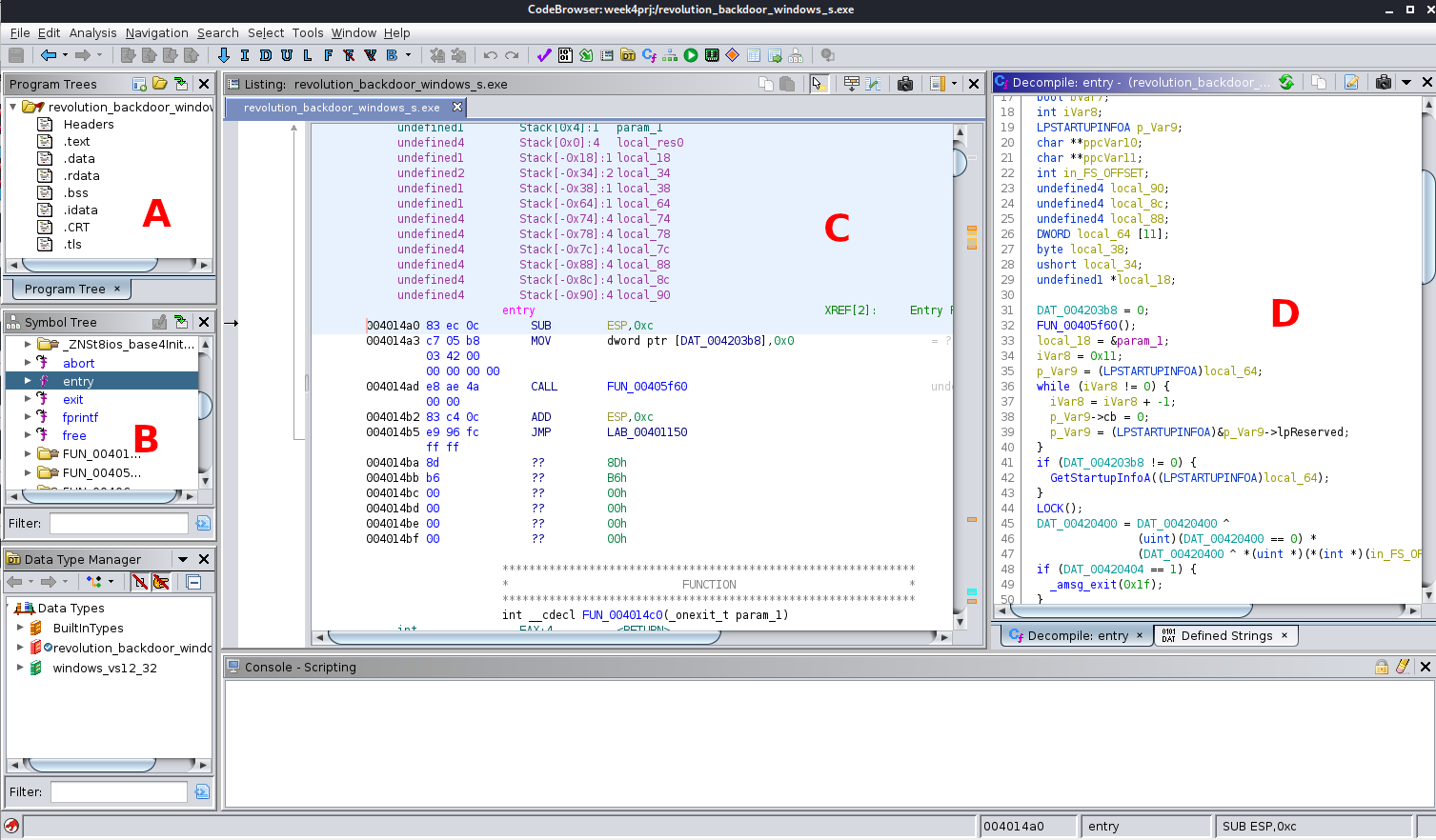
A day with Ghidra. Reverse engineering, M9 in the list of… | by Siddharth Shivkumar | WriteaByte | Medium

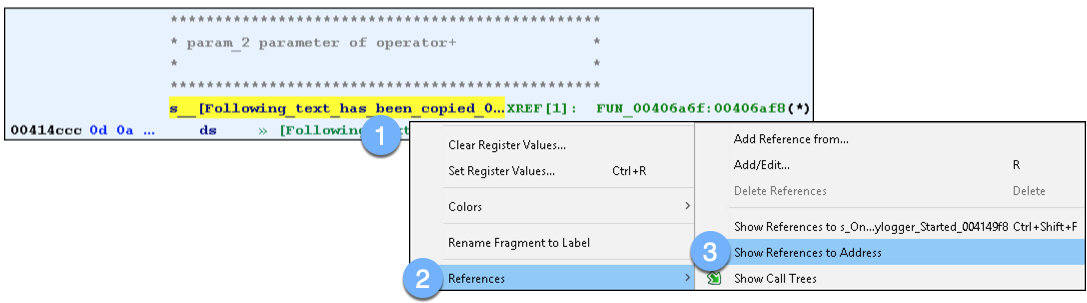
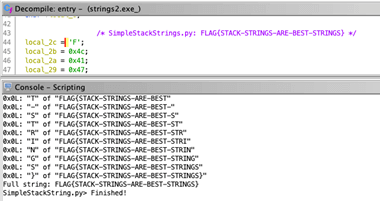
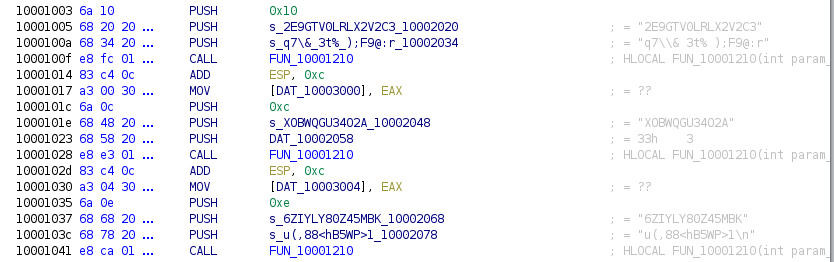
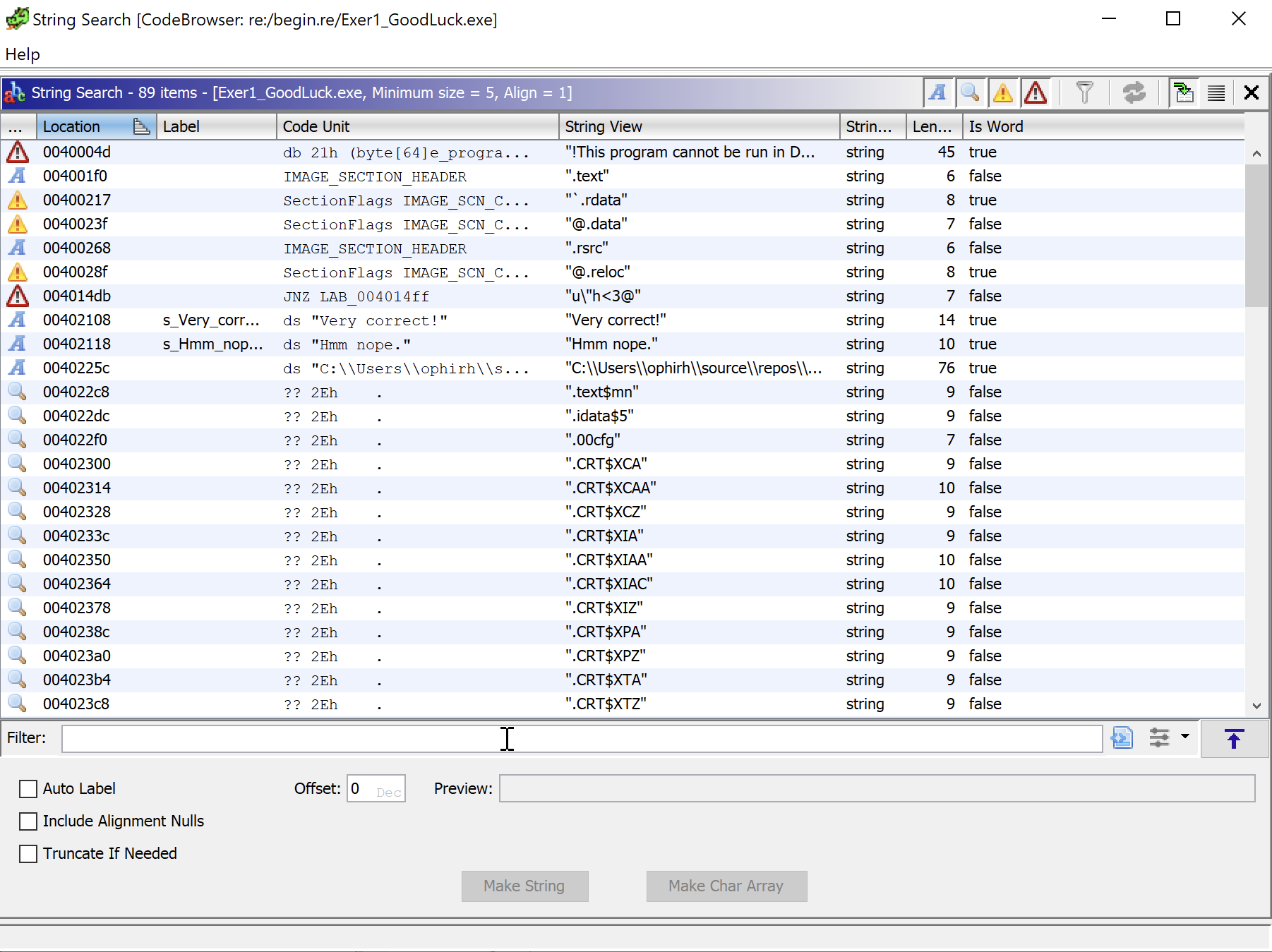
Is there any way to make the decompiler show the string pointer instead of the memory address as a number? The disassembly shows the string just fine, so why can't the decompiler? :

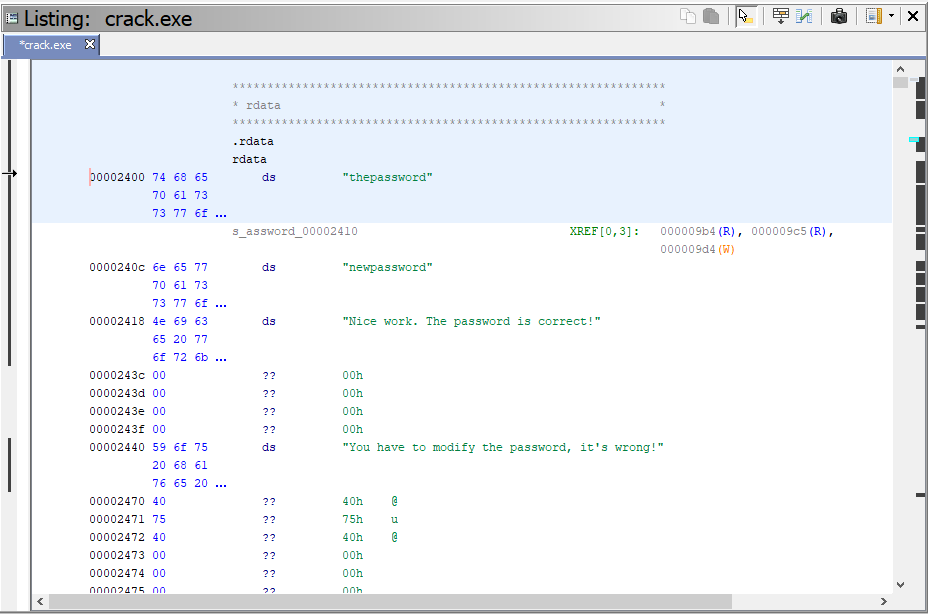
Differences between hex-editor and Ghidra and how to find strings - Reverse Engineering Stack Exchange